Russian Strategic Information Attack: The Dark Covenant Between State and Cybercriminals

Imagine a scenario where one day ATMs stop working, entire districts go dark, and phones fall silent. Conflicting government messages appear on TV screens while panic spreads through social media. Sounds like a disaster movie plot? According to latest analyses, this is exactly what the first day of a Russian strategic information attack might look like.
In the Shadow of Nuclear Arsenal
While the world focuses on Russia's nuclear potential, a much more sophisticated weapon is being developed in Moscow's institutes. The Russian strategic information attack represents a new military doctrine that allows the Kremlin to achieve strategic goals without launching missiles or moving troops.
The Dark Covenant
A key, often overlooked element of Russia's arsenal is the so-called "Dark Covenant" - a system of informal connections between the Russian state and the cybercriminal world. This unique alliance takes three main forms:
Direct Connections
The FSB and other Russian services actively recruit talented hackers directly from the criminal environment. The story of Dmitry Dokuchaev, an FSB major who was recruited after previous criminal activity, illustrates how fluid the boundary is between the criminal and state worlds in Russian cyberspace.
As revealed by a former hacker quoted by journalist Daniil Turovsky, the FSB Information Security Center has such limited technical staff that it regularly employs external specialists, sometimes hiding them in safe houses.
Indirect Links
The Russian state uses cybercriminals' tools and infrastructure to conduct its own operations. An example is the use of malware available on Russian-language hacking forums, such as DarkCrystal RAT or WarZoneRAT, by groups linked to Russian intelligence.
Tacit Consent
The most subtle form of cooperation is the Russian state turning a blind eye to cybercriminal activity as long as it serves its strategic interests. Criminal groups can operate freely provided they don't attack targets on Russian territory and support - knowingly or not - Russian geopolitical goals.
This cooperation has taken on a new dimension since the full-scale invasion of Ukraine. Some cybercriminal groups, like Conti, openly declared loyalty to the Kremlin. Others, like the supposedly independent "hacktivist" groups Killnet or XakNet Team, conduct information operations supporting Russian objectives, likely in close coordination with Russian services.
Particularly interesting is the case of APT44 (also known as Sandworm Team), which coordinates its activities with seemingly independent "hacktivists". Analysts have observed cases where after APT44's cyberattacks on Ukrainian targets, the same data appeared on Telegram channels of allegedly independent hacker groups within 24 hours.
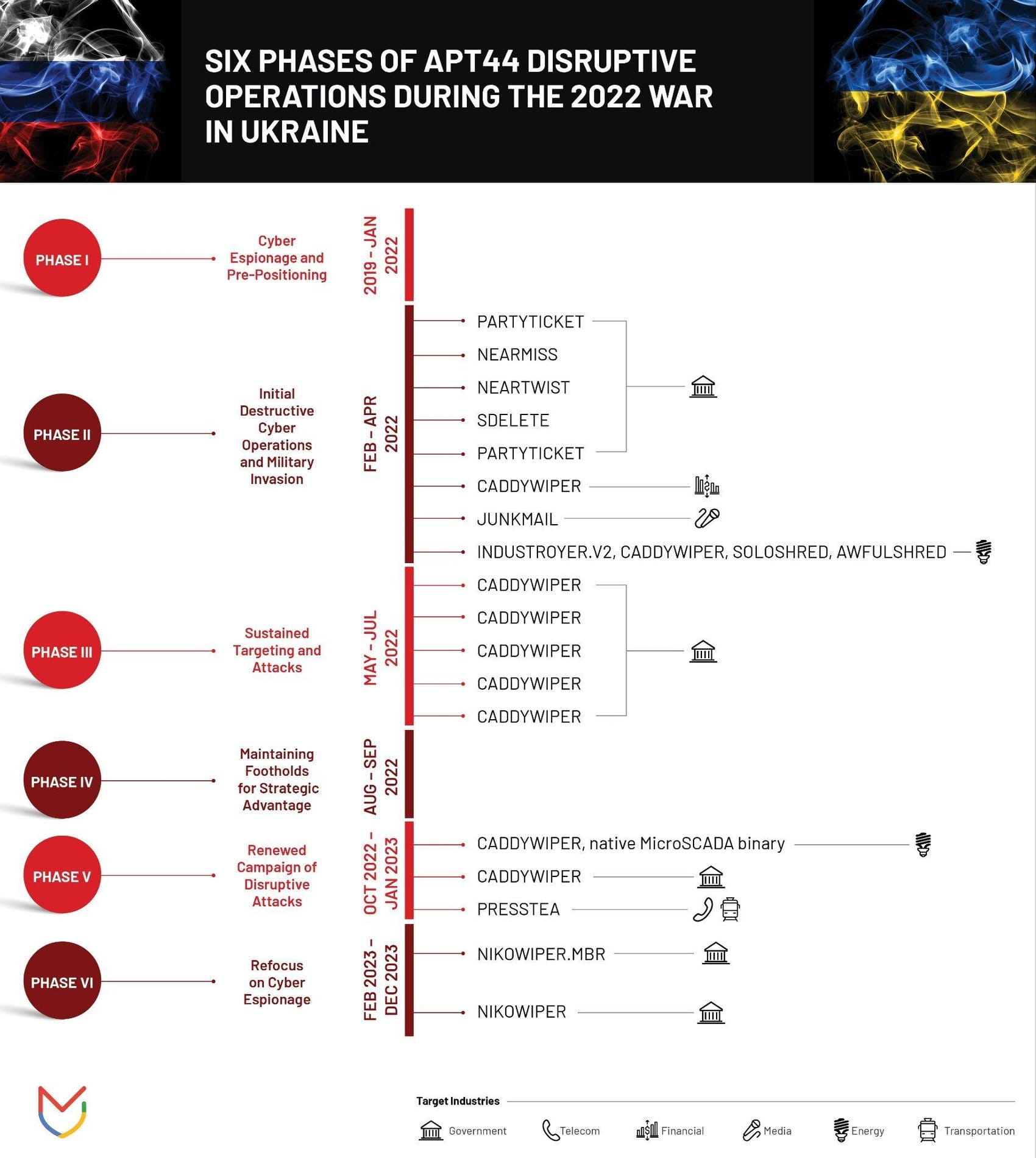
Evolution of Tactics
Russian cyber operations have undergone significant evolution, particularly after the full-scale invasion of Ukraine. Observed changes include:
- Transition from complex, long-term operations to more aggressive, short-term campaigns
- Emergence of seemingly independent "hacktivist" groups like Killnet and XakNet Team
- Close coordination between official state structures and criminal groups
What is Strategic Information Attack?
According to the latest Recorded Future report, a global leader in threat intelligence, Russia is developing an advanced concept of strategic information attack (SIA) that may pose as serious a threat as nuclear weapons. This in-depth analysis, published in October 2024, sheds new light on how the Kremlin plans to conduct future conflicts.
The Russian strategic information attack (SIA) is a concept of using non-kinetic means to inflict strategic-level losses on an adversary. According to Recorded Future analysts, this is a weapon reserved for "full-scale war", comparable in its effects to strategic nuclear weapons.
Crucially, SIA consists of two main components:
- Psychological attack (strategic influence operations)
- Technical attack (strategic cyberattack)
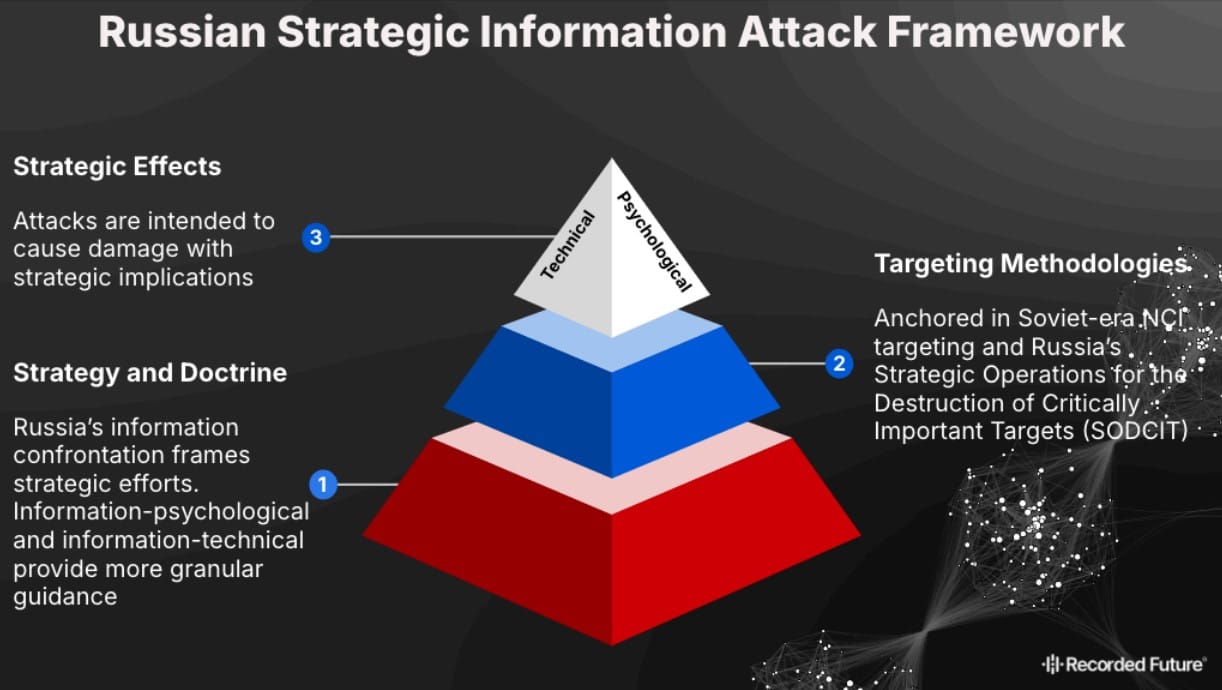
Doctrinal Foundation of the Concept
Although Russia doesn't have a single, publicly available doctrinal document dedicated to SIA, the concept is deeply rooted in Russian strategic thinking. According to official military doctrine, Russia defines four levels of conflict:
- Full-scale war (highest level)
- Regional war
- Local war
- Armed conflict (lowest level)
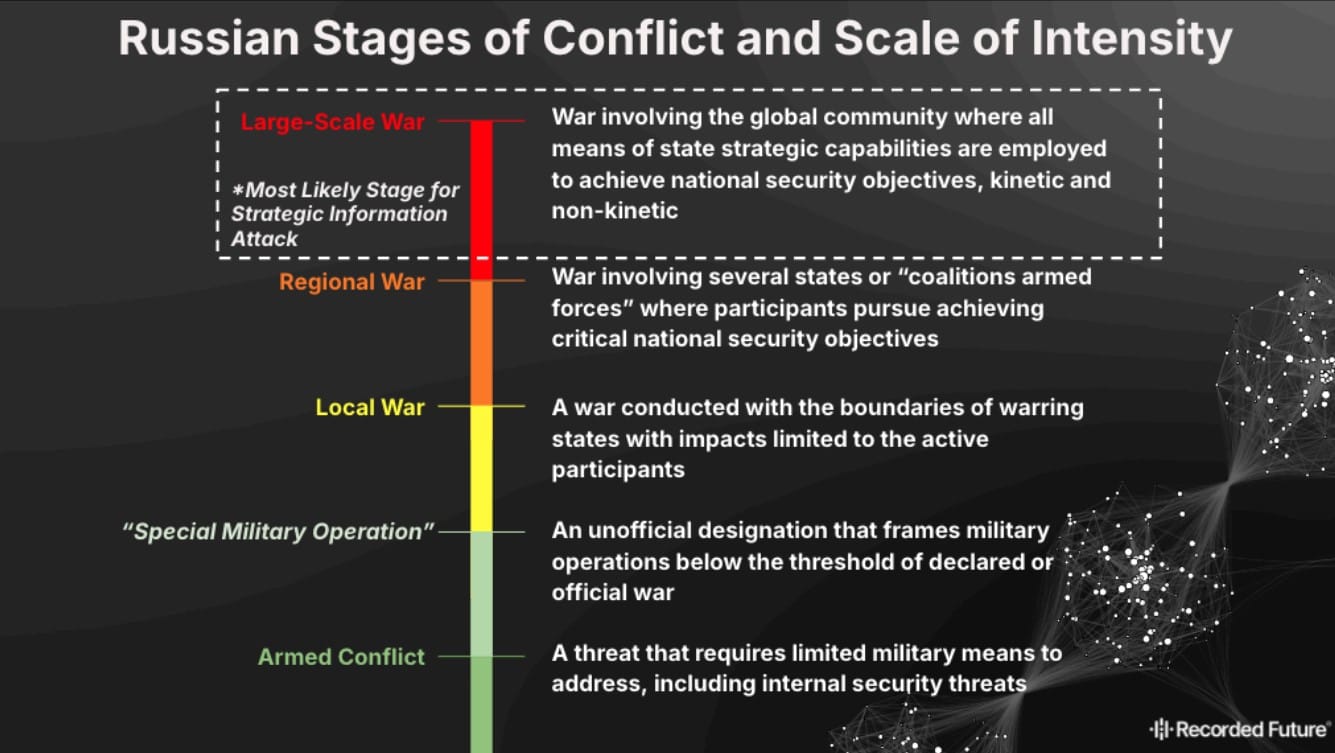
SIA is a tool reserved for the highest level of conflict, where it can be used in parallel with other strategic means, including nuclear weapons.
The Gerasimov Doctrine - Operational Support Concept
Often misinterpreted as Russia's new military doctrine, the so-called "Gerasimov Doctrine" is actually just an operational concept supporting broader state strategy. Presented in 2013 by General Valery Gerasimov, Chief of the General Staff of the Russian Armed Forces, it is neither a doctrine nor the driving force behind Russian foreign policy. Rather, it represents an attempt to develop a comprehensive operational concept for Russia's national security establishment in its confrontation with the West. Gerasimov described ways of combining elements of "soft" and "hard" power across various domains, transcending traditional boundaries between states of war and peace. However, it's crucial to understand that in line with Russian civil-military traditions, the military has never been the driving force behind Russian national security policy, but rather its implementer.
The Primakov Doctrine - Strategic Foundation
The true foundation of Russian foreign and defense policy for over two decades has been the "Primakov Doctrine", named after former foreign minister and prime minister Yevgeny Primakov. It posits that a unipolar world dominated by the United States is unacceptable to Russia and formulates three fundamental principles:
- Pursuit of a multipolar world managed by a concert of powers capable of balancing U.S. unilateral power
- Maintaining Russia's primacy in the post-Soviet space and leading integration processes in this region
- Opposition to NATO expansion
In practice, this doctrine defines Russia's strategic objectives and frameworks for all state actions in the international sphere - both diplomatic and military. Importantly, its implementation is by no means reckless - Russia's use of both hybrid means and conventional military force (for example, in Georgia in 2008 and Ukraine since 2014) has always been carefully calculated to avoid excessive risk.
SIA Mechanism
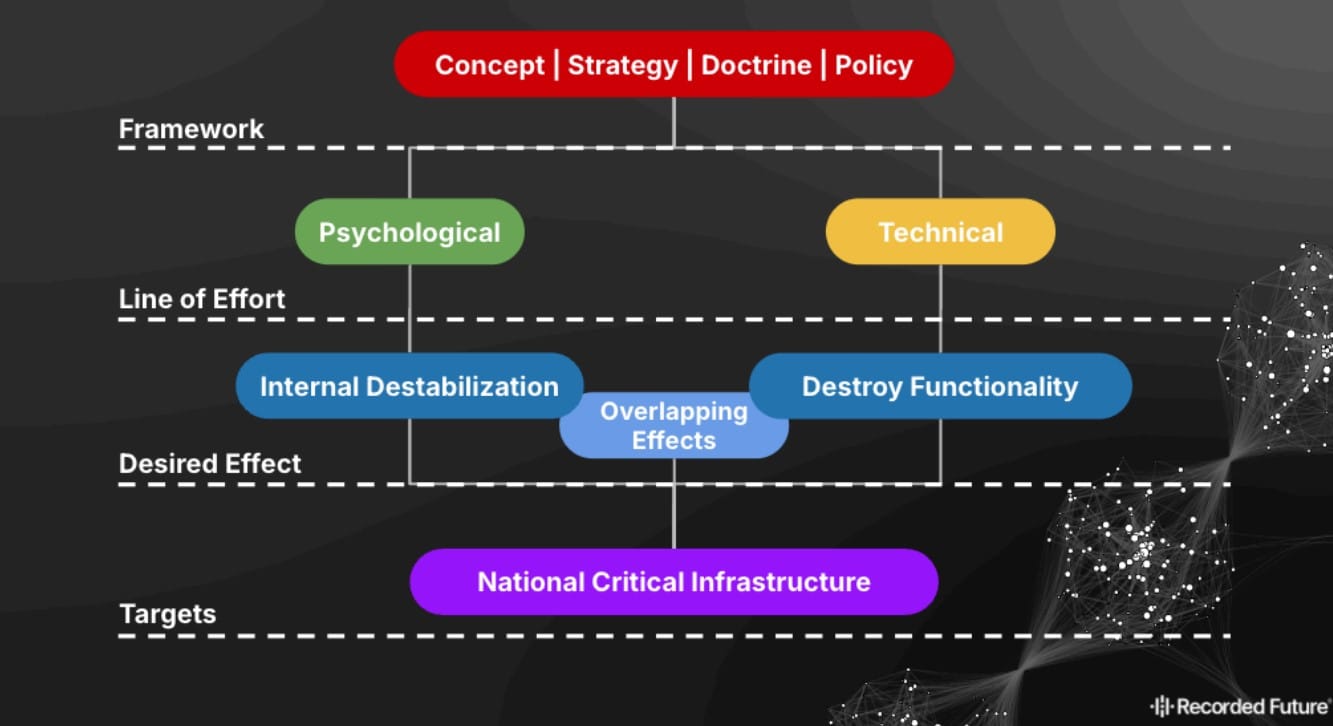
According to Recorded Future report sources, Russia uses an anthropomorphic targeting model originating from Soviet times. This model divides attack targets into four categories:
- "Brain and its deputies" (national and local leadership)
- "Nervous system" (national communication)
- "Heart and circulatory system" (energy infrastructure)
- "Teeth" (nuclear capabilities)
Psychological Component
The psychological attack within SIA aims to destabilize the internal situation of the target country. According to the Recorded Future report, Russia is considering using artificial intelligence (MUAI - Malicious Use of Artificial Intelligence) to:
- Create convincing deepfakes depicting state leaders
- Mass produce personalized disinformation content
- Undermine the "psychological security" of the target society
The Kremlin believes that a properly conducted psychological attack could even lead to the "balkanization" of the target state or trigger civil war.
Technical Component
Alongside the psychological attack, SIA assumes conducting coordinated cyberattacks on the adversary's critical infrastructure. The goal is not temporary disruption of systems but causing long-lasting and extensive damage to:
- Energy systems
- Communication infrastructure
- Banking and financial systems
- Government and military networks
Targeting Model
Russia employs an anthropomorphic targeting model that categorizes objectives into four key areas:
- Leadership and command structures ("Brain and deputies")
- National communications network ("Nervous system")
- Energy infrastructure ("Heart and circulatory system")
- Strategic nuclear capability ("Teeth")
"Escalation for De-escalation" Strategy
A key element of the SIA concept is its role in Russia's "escalation for de-escalation" strategy. Recorded Future emphasizes that the goal is not total destruction of the adversary, but rather forcing them to negotiate on Moscow's terms through:
- Triggering a crisis that exceeds the adversary's tolerance threshold
- Demonstrating the capability to inflict even greater losses
- Offering de-escalation in exchange for political concessions
Potential Usage Scenarios
The Recorded Future report presents a hypothetical scenario of SIA deployment in a conflict with NATO:
Psychological Attack:
- Mass influence operations exploiting social divisions
- Utilization of MUAI (malicious use of artificial intelligence) to create false crisis communications
- Spreading panic through disinformation about nuclear attacks
- Undermining trust in financial institutions and state authorities
Technical Attack:
- Paralysis of communication systems (telephony, internet, radio)
- Disruption of energy supplies
- Blockade of banking systems
- Disruption of supply chains
This comprehensive approach combines psychological and technical elements to achieve maximum strategic effect while maintaining plausible deniability and avoiding direct military confrontation.
Implications for International Security
As Recorded Future analysts emphasize, Russia's strategic information attack presents an unprecedented challenge in its scale and complexity. It combines traditional influence methods with modern digital techniques, while simultaneously utilizing the potential of the criminal world to achieve state objectives.
Effective defense requires action in several key areas:
Understanding the Threat
- Complete recognition of Russia's capabilities spectrum, from cyberattacks to social manipulation
- Awareness of the "Dark Covenant" and its implications for international security
- Anchoring defensive strategies in deep understanding of Russian doctrine
Development of Defensive Capabilities
- Building redundancy in critical infrastructure systems
- Developing technologies for detecting and countering MUAI (malicious use of artificial intelligence)
- Creating comprehensive defense strategies addressing both technical and psychological aspects
International Cooperation
- Coordinating detection and counter-attack activities
- Sharing threat information between partners
- Building joint defensive potential within alliances
It is crucial to understand that effective defense against SIA requires a holistic approach combining traditional cybersecurity measures with modern methods of countering influence operations and social manipulation.
When Reality Resembles a Spy Thriller
While preparing this article, I often found myself reading subsequent sources and reports with flushed cheeks, as if I were delving into the best spy thriller. The difference being that this isn't literary fiction, but the brutal reality of today's world. Never before had state-sponsored threat actors been so tangible and clear to me as when I traced the development of Russia's strategic information attack.
Every fake news item in my feed, every dubious deepfake, or suspicious narrative in social media takes on entirely new meaning when you understand the broader context - these aren't random actions or chaotic disinformation. They are precisely orchestrated elements of a larger whole, where the cybercriminal world intertwines with the state apparatus under the "Dark Covenant," and traditional influence operations combine with the latest technology achievements.
This analysis was a true research expedition for me - from technical details of cyberattacks, through complex military doctrines, to the psychology of mass manipulation. Countless threads and sources come together in a story so fascinating it's hard to believe it's true. And yet - as often happens - the best stories are written by life itself.
I hope that for you too, this journey through the meanders of Russian SIA was equally fascinating. I encourage you to reach for the full versions of Recorded Future reports and other sources. This is reading that not only broadens horizons but also changes how we look at contemporary threats in cyberspace and beyond.
Member discussion