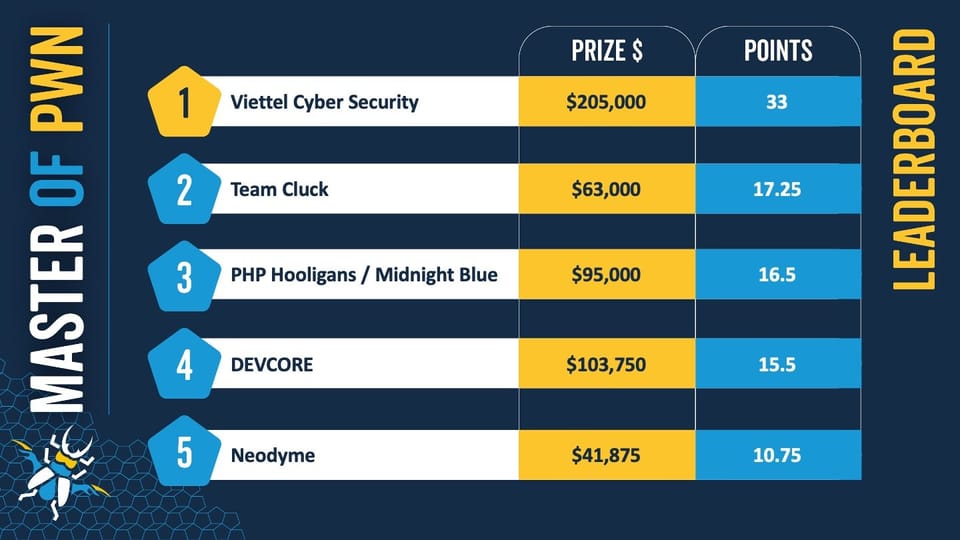
Pwn2Own Ireland 2024: Over a million dollars for discovering 70 security vulnerabilities
The first-ever Pwn2Own competition in Ireland took place from October 22-25, 2024. The event marked a significant milestone - cybersecurity experts discovered over 70 unique zero-day vulnerabilities in popular devices, earning rewards totaling $1,066,625.
Categories and attack targets
The competition covered seven main device categories:
- Network Attached Storage (NAS)
- Surveillance systems and cameras
- Printers
- Smart speakers
- Mobile phones
- Home automation hubs
- SOHO (Small Office/Home Office) networks
The SOHO SMASHUP category emerged as a highlight of the competition, where participants had to perform complex chain attacks, taking control of multiple devices simultaneously.
Day by day: Competition progress
Day one (October 22)
Number of attempts: 12 Successful exploits: 8 Notable achievements:
- Viettel Cyber Security exploited the Lorex 2K WiFi camera (prize: $30,000)
- successfully executed a complex SOHO SMASHUP attack chain using 9 vulnerabilities (prize: $100,000)
- Jack Dates took control of the Sonos Era 300 speaker (prize: $60,000)
- Team Neodyme exploited the HP Color LaserJet Pro MFP 3301fdw printer (Prize: $20,000)
Day two (October 23)
Number of attempts: 15 Successful exploits: 9 Notable achievements:
- Ken Gannon hacked the Samsung Galaxy S24 using 5 vulnerabilities and installing an app that gave him shell access (prize: $50,000)

- Team Neodyme conducted a successful SOHO Smashup attack using 4 vulnerabilities (prize: $21,875)
- NiNi from DEVCORE took control of the AeoTec hub (prize: $40,000)
Day three (October 24)
Number of attempts: 10 Successful exploits: 8 Notable achievements:
- Computest Sector 7 used 4 vulnerabilities in a SOHO SMASHUP attack (prize: $25,000)
- PHP Hooligans compromised the QNAP system and Lexmark printer (prize: $25,000)
- DEVCORE Research Team took control of Synology BeeStation (prize: $20,000)
Day four (October 25)
Number of attempts: 4 Successful exploits: 3 Notable achievements:
- Team Cluck performed a SOHO SMASHUP attack using 6 vulnerabilities (prize: $23,000)
- PHP Hooligans demonstrated a creative Lexmark printer exploit by playing a melody on it (prize: $10,000)
- Team Smoking Barrels and Viettel Cyber Security exploited TrueNAS Mini X (prizes of $20,000 each)
Final statistics

- Total prize pool: $1,066,625
- Number of vulnerabilities detected: over 70
- Master of Pwn winner: Viettel Cyber Security (33 points)
- Winner's prize: $205,000
Vendors' rapid response to detected vulnerabilities
Significant note was the swift response from NAS hardware manufacturers. Synology and QNAP, two leading storage solution providers, released patches at record speed:
- Synology released updates within 48 hours of vulnerability demonstration
- QNAP patched two critical vulnerabilities within a week
- Other manufacturers have the standard 90 days to release fixes
Key Synology updates: RISK:STATION threatens millions of devices
A critical vulnerability in Synology's photo application drew particular attention during Pwn2Own Ireland 2024, discovered in just two hours by Dutch researcher Rick de Jager from the Midnight Blue team. The vulnerability, designated as CVE-2024-10443 and named RISK:STATION, presented significant security implications for several reasons.
Vulnerability characteristics
RISK:STATION is a zero-click vulnerability, meaning no user interaction is required for exploitation. Moreover, it affects applications installed by default on Synology NAS devices, specifically:
- BeePhotos for BeeStation OS 1.1 (updated to 1.1.0-10053)
- BeePhotos for BeeStation OS 1.0 (updated to 1.0.2-10026)
- Synology Photos 1.7 for DSM 7.2 (updated to 1.7.0-0795)
- Synology Photos 1.6 for DSM 7.2 (updated to 1.6.2-0720)
Scale of the threat
The Midnight Blue team's investigation uncovered:
- Hundreds of thousands of Synology NAS devices are directly connected to the internet
- Millions more devices are potentially vulnerable through the QuickConnect service
- The vulnerability requires no authentication to exploit
- Attackers can gain root access to the device
Attack mechanism
A key security concern is that the vulnerability can be exploited in two ways:
- Through direct access to an internet-connected device
- Through Synology's QuickConnect service, which enables remote NAS access
The vulnerable part of the application requires no authentication, meaning attackers can exploit the vulnerability directly over the internet without needing to bypass any access controls.
Potential consequences
A successful attack can lead to:
- Theft of personal and corporate data
- Installation of backdoors
- System encryption by ransomware
- Integration of infected devices into a botnet
Manufacturer's response
Synology demonstrated remarkable response time:
- Patches were released within 48 hours of notification
- Two security bulletins were published (October 25)
- The vulnerability was marked as "critical"
However, several challenges remain with the update deployment:
- No automatic updates in Synology NAS devices
- Unclear number of users aware of the patch
- Patch publication may facilitate vulnerability identification by cybercriminals
Key QNAP updates
QNAP fixed:
- SQL Injection vulnerability (CVE-2024-50387) in SMB service
- Command Injection vulnerability (CVE-2024-50388) in HBS 3 Hybrid Backup Sync
Behind the scenes: Lessons learned from Pwn2Own Ireland 2024
The findings by the Midnight Blue team shed an alarming light on critical infrastructure security vulnerabilities. Their investigation revealed unsecured Synology devices across sensitive locations - from police departments in the US and Europe to critical infrastructure contractors in South Korea and strategic facilities in Italy and Canada.
While some manufacturers demonstrated impressive response times - with Synology delivering patches within 48 hours and QNAP following within a week - the nature of the vulnerabilities raises serious concerns. The discovery of hardcoded cryptographic keys, unsecured communication channels, and basic SQL injection vulnerabilities points to fundamental security design issues rather than sophisticated technical oversights.
Looking ahead, Pwn2Own shifts its focus to automotive security with its next event scheduled for January 22-24, 2025, in Tokyo.
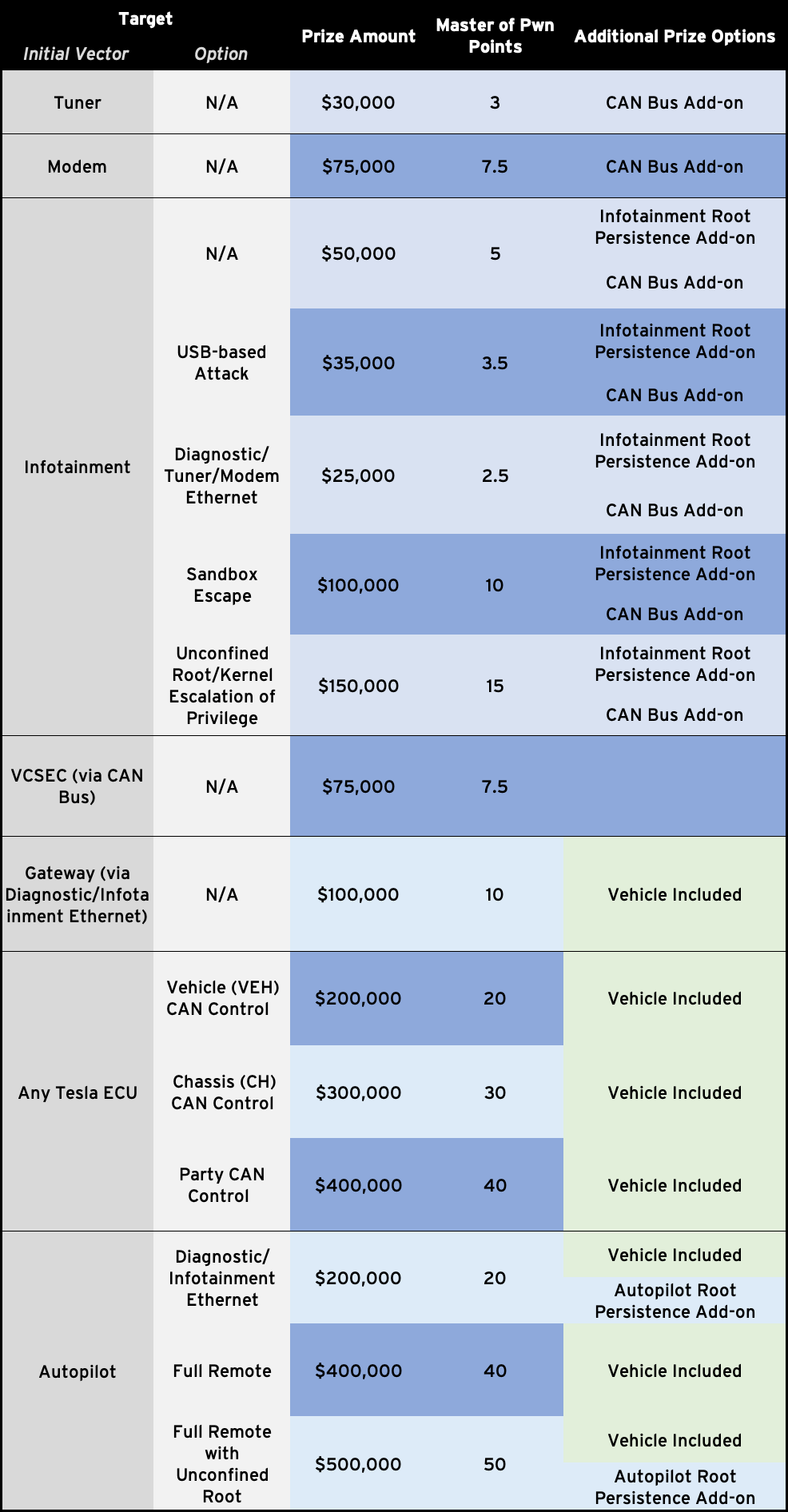
The competition will feature four key categories:
- Tesla
- In-Vehicle Infotainment systems (IVI)
- Electric vehicle chargers
- Operating systems
As we anticipate this automotive-focused edition, a crucial question emerges: do such contests serve as guardians of security or potential threat multipliers? While they enable the discovery and patching of critical vulnerabilities before malicious exploitation, they also expose weaknesses in life-critical systems. The stakes have clearly risen - where NAS vulnerabilities might lead to financial losses, automotive security flaws could have far more severe consequences. Only time will tell...
Member discussion