Midnight Blizzard Conducts Largest-Ever Phishing Campaign Using RDP Files

On October 22, 2024, Microsoft Threat Intelligence discovered an unprecedented phishing campaign conducted by Midnight Blizzard, also known as APT29 or Cozy Bear. The group, officially linked by US and UK governments to Russia's Foreign Intelligence Service (SVR), has this time targeted thousands of users across more than 100 organizations worldwide.
Key campaign characteristics:
- Massive scale of operations encompassing hundreds of organizations
- Use of RDP files signed with LetsEncrypt certificates
- Advanced social engineering techniques
- Impersonation of well-known technology brands
Innovative Attack Mechanism
This campaign significantly differs from the group's previous operations, known for precise targeting of specific institutions. Midnight Blizzard is now using an innovative technique based on Remote Desktop Protocol (RDP) configuration files, signed with LetsEncrypt certificates. This new approach poses a serious threat to the security of global organizations.
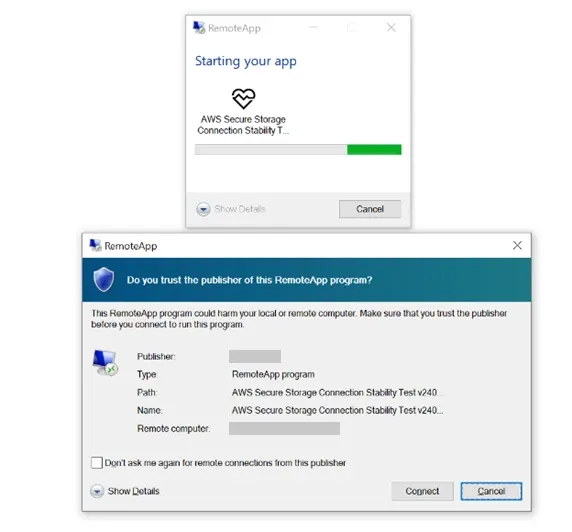
Attack sequence:
- Victim receives a crafted email message
- Upon opening the attached RDP file, an automatic connection to the C2 server is established
- The system is configured for bidirectional resource mapping
- Attackers gain broad access to victim resources
Unlike traditional phishing attacks that typically attempt to steal credentials through fake login pages, this campaign employs a much more sophisticated mechanism. When the victim opens the malicious RDP file, an automatic connection is established with attacker-controlled servers. The victim's system is then configured for bidirectional resource mapping, giving the attackers virtually unlimited access to the compromised computer.
Compromise scope:
- All logical drives
- Clipboard contents
- Printers and peripheral devices
- Windows authentication mechanisms
- Smart cards
This comprehensive access demonstrates advanced operation planning and deep understanding of Windows architecture by the Midnight Blizzard group.
History of Midnight Blizzard Operations
FoggyWeb (2021)
In 2021, Microsoft identified FoggyWeb malware, a backdoor targeting Active Directory Federation Services (ADFS) servers that enabled:
- Remote exfiltration of configuration databases
- Certificate interception
- Installation of additional malware components
A year later, the group expanded its capabilities by introducing an even more advanced tool - MagicWeb, which could manipulate the authentication process itself in AD FS.
MagicWeb (2022)
Enhancement of predecessor's capabilities with:
- Authentication process manipulation
- Certificate modification
- MFA security bypass
This evolution of tools and tactics shows systematic building of Russian intelligence operational capabilities in cyberspace. Each subsequent campaign introduces new, innovative attack methods while building on proven techniques from previous operations.
Attack Infrastructure
In the current campaign, the group uses a number of previously compromised email domains to send malicious messages. The phishing employs advanced social engineering techniques, often impersonating Microsoft employees or other cloud service providers. Malicious file names, such as "AWS IAM Compliance Check.rdp" or "Zero Trust Architecture Configuration.rdp", have been carefully chosen to gain recipients' trust.
Phishing domains used:
- sellar[.]co.uk
- townoflakelure[.]com
- totalconstruction[.]com.au
- swpartners[.]com.au
- cewalton[.]com
Malicious file names:
- AWS IAM Compliance Check.rdp
- AWS IAM Configuration.rdp
- AWS IAM Quick Start.rdp
- AWS SDE Compliance Check.rdp
- AWS SDE Environment Check.rdp
- AWS Secure Data Exchange – Compliance Check.rdp
- AWS Secure Data Exchange Compliance.rdp
- Device Configuration Verification.rdp
- Device Security Requirements Check.rdp
- IAM Identity Center Access.rdp
- IAM Identity Center Application Access.rdp
- Zero Trust Architecture Configuration.rdp
- Zero Trust Security Environment Compliance Check.rdp
- ZTS Device Compatibility Test.rdp
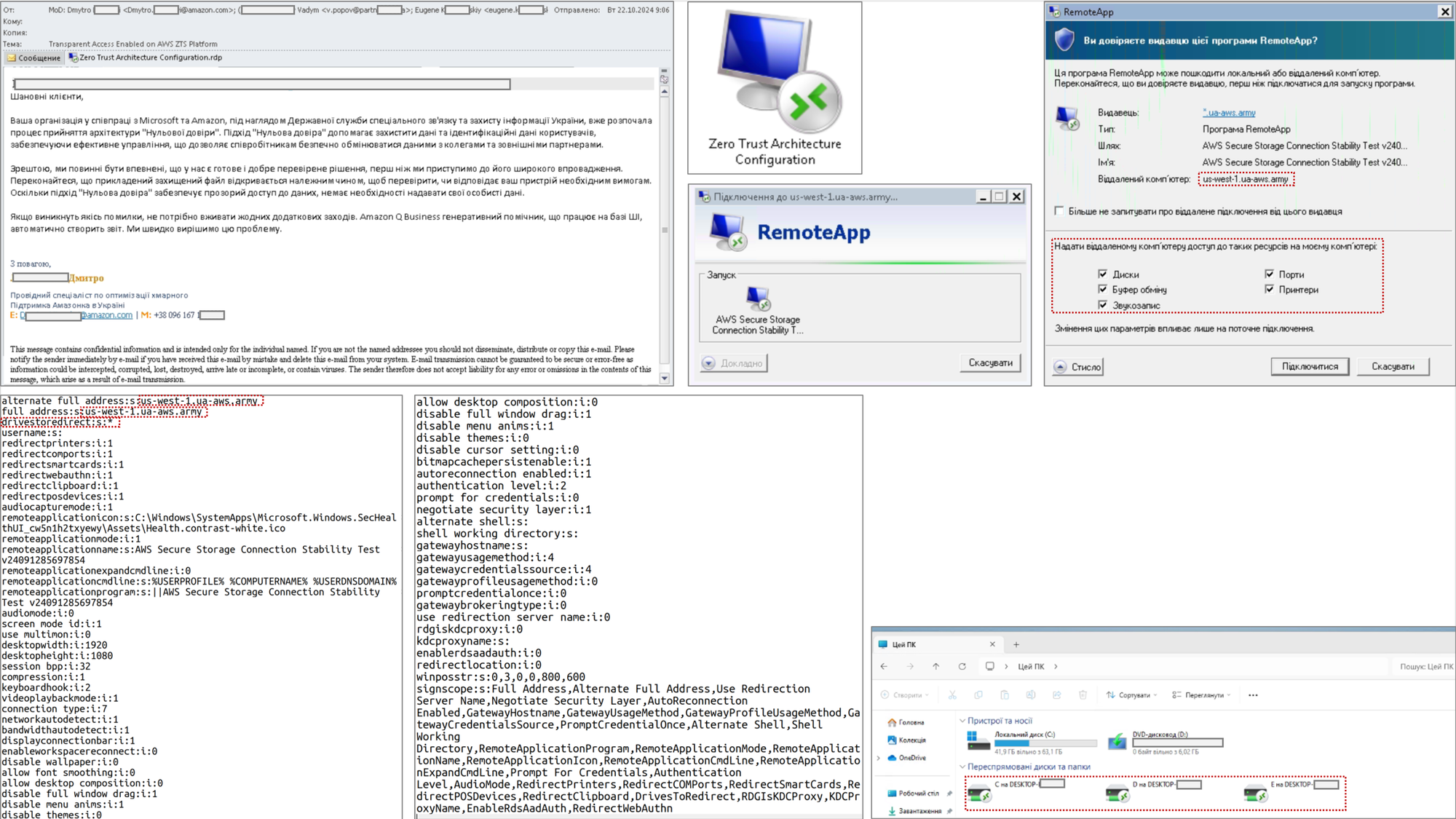
Particularly concerning is how the group utilizes its command & control infrastructure. Hundreds of C2 domains have been registered to mimic legitimate government, military, and international institutions. This technique of masking malicious infrastructure significantly complicates attack detection and blocking. According to Amazon Web Services report, some domains attempted to impersonate official AWS resources, though the goal wasn't to steal Amazon service credentials, but rather to obtain Windows authentication.
Example domain names:
- ap-northeast-1-aws.s3-ua[.]cloud
- ca-central-1.ua-gov[.]cloud
- eu-central-1-aws.gov-pl[.]cloud
- eu-central-1-aws.amazonsolutions[.]cloud
- eu-central-2-aws.gov-pl[.]cloud
- eu-east-1-aws.mil-pl[.]cloud
- eu-east-1-aws.ukrtelecom[.]cloud
- eu-south-2-aws.msz-pl[.]cloud
Geopolitical Context of the Threat
According to the latest report from FBI, NSA, CNMF, and British NCSC-UK, Midnight Blizzard particularly targets:
- Government organizations
- Defense sector
- Technology companies
- Financial institutions
- Think tanks
- International organizations
Geographic scope of attacks:
Microsoft emphasizes that the current campaign is part of a larger intelligence operation, likely connected to Russia's invasion of Ukraine. Since 2021, there has been a significant increase in SVR cyber espionage activity targeting organizations supporting Ukraine. According to the latest reports, the group is particularly interested in organizations in countries such as:
- United Kingdom
- Europe
- Australia
- Japan
- Organizations supporting Ukraine
Polish Context of Midnight Blizzard Operations
Analysis of the infrastructure used by Midnight Blizzard sheds interesting light on the group's potential targets. Among hundreds of domains used in the campaign, we find: gov-pl, mil-pl, msz-pl. These names, imitating Polish government and military institutions, indicate that Polish organizations have also fallen within the scope of Russian cyber operations.
This is not surprising in light of findings contained in the FBI, NSA, CNMF, and NCSC-UK report, according to which Midnight Blizzard systematically targets state institutions, defense organizations, and think tanks in Europe. The group pays particular attention to organizations involved in supporting Ukraine, and Poland, as one of the key partners supporting Ukraine, naturally may be a target of such activities.
Conclusions and Perspectives
The Midnight Blizzard campaign demonstrates the systematic evolution of cybersecurity threats. From sophisticated backdoors like FoggyWeb, through authentication process manipulation in MagicWeb, to mass campaigns using RDP files - each subsequent operation by the group shows the growing technical capabilities of Russian intelligence.
Member discussion