Intel Under Chinese Authorities' Scrutiny - Global Tech War Enters New Phase
October 2024 marked a turning point in the ongoing technological war between world powers. The Cyber Security Association of China (CSAC) called for a comprehensive review of Intel processors sold in China, citing "frequent security vulnerabilities and high failure rates." Particular concerns were raised about vulnerabilities in games such as GhostRace, NativeBHI, and Downfall, which could allow attackers to access sensitive information through speculative code execution mechanism flaws.
China's Ministry of State Security (MSS) immediately supported these allegations, issuing a warning about "increasingly evident cybersecurity threats and risks permeating various fields from politics and economy to national defense." This unprecedented action against the American technology giant is not an isolated incident.
Behind the Chinese Investigation
Just a few days earlier, on October 14, the National Computer Virus Emergency Response Center released a devastating report exposing the details of American cyber espionage operations. The document revealed the existence of an advanced tool codenamed "Marble," specifically designed to mask traces of cyberattacks and falsely attribute them to other nations. This framework, developed no later than 2015, allows for the insertion of misleading indicators suggesting involvement of other countries, including China, Russia, Korea, Iran, and Arab nations.
"These are not random discoveries," claims an anonymous expert cited in the report. "American intelligence agencies, acting like chameleons in cyberspace, systematically conduct espionage operations under false flags, attempting to shift responsibility to other countries."
The Road to Escalation - A History of Mutual Accusations
To understand the current escalation, we must go back to May 2023, when the Five Eyes alliance made joint accusations against China. In an unprecedented move, the United States, United Kingdom, Australia, Canada, and New Zealand issued a security alert regarding an alleged Chinese hacking group known as Volt Typhoon. Microsoft, simultaneously publishing its own report, claimed that the group "focuses on espionage and information gathering," particularly targeting critical U.S. infrastructure in Guam and other regions.
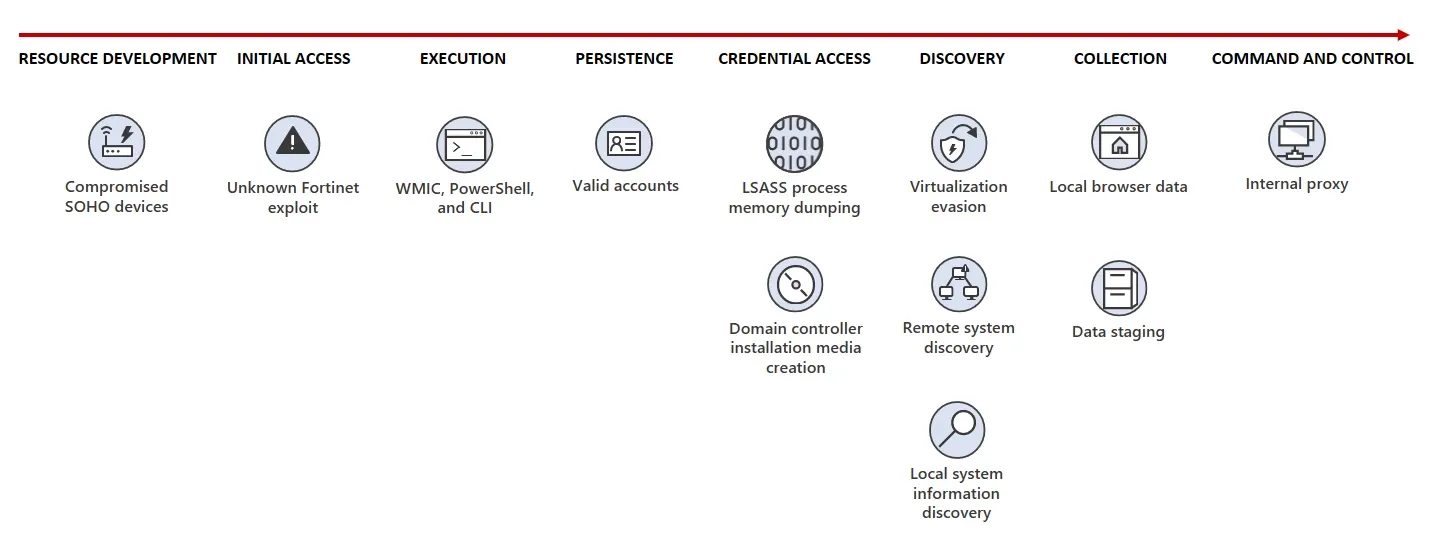
According to Microsoft's report, the group had been operating since mid-2021, systematically infiltrating sectors including communications, manufacturing, media, transportation, construction, IT, and education. Microsoft expressed "significant concerns" about the potential impact of these activities on their customers, suggesting that the group aims to develop capabilities to disrupt critical communication infrastructure between the U.S. and the Asia region during future crises.
Particular concern was raised by the group's advanced operational techniques. Instead of traditional malware, the attackers primarily utilized legitimate system tools (known as living-off-the-land techniques) and conducted manual operations through command lines. Their activities focused on three main areas: collecting data and credentials from local and network systems, archiving stolen information for later exfiltration, and using stolen credentials to maintain long-term access.
Microsoft detailed how the group exploited vulnerabilities in Fortinet FortiGuard devices to gain initial access, then used compromised small office and home office (SOHO) network devices - including routers from ASUS, Cisco, D-Link, NETGEAR, and Zyxel - as proxies to mask their network traffic. The group also reportedly employed custom versions of open-source tools to establish command and control (C2) channels.
However, a detailed investigation by Chinese institutions cast an entirely new light on the matter. Reports published in April and July 2024 by the National Computer Virus Emergency Response Center and 360 Digital Security Group demonstrated that the narrative about "Chinese sponsorship" of Volt Typhoon was a carefully orchestrated disinformation campaign.
The Chinese experts analyzed the technical details of the operations, including the use of LSASS (Local Security Authority Subsystem Service) memory dump tools, attempts to create domain controller installation media using Ntdsutil.exe, and the use of tools such as Impacket and Fast Reverse Proxy (FRP). Their findings indicated that the group's operational patterns were more characteristic of an organized ransomware group than a state-sponsored operation. Moreover, analysis of five key IP addresses linked to the attacks revealed connections to the Dark Power cybercriminal group, which targeted entities worldwide without any clear geographical or sectoral focus.
The Anatomy of Manipulation
The technical analysis presented in the reports revealed several irregularities in the American accusations:
- Out of 29 malware samples attributed to Volt Typhoon, only 13 could be verified on the independent VirusTotal platform
- Investigation of five key IP addresses showed connections not to Chinese government agencies, but to the Dark Power ransomware group
- ThreatMon, in its April 2023 report, linked these same IP addresses to attacks on institutions in Algeria, Egypt, Czech Republic, Turkey, Israel, Peru, France, and the United States
"There was no connection to any specific country or sector," emphasizes the report, debunking the theory of state sponsorship.
History Repeats Itself
These discoveries gain additional significance in the context of previous U.S. actions against the Chinese technology sector. In 2020, the American administration blacklisted dozens of Chinese companies, including:
- SenseTime - the world's largest AI startup
- Megvii - an IoT solutions specialist
- CloudMinds - an AI-controlled robotics creator
- Qihoo 360 - a cybersecurity company
The official reason was national security concerns and alleged connections to the Chinese surveillance apparatus. However, as recent discoveries show, it is the United States that operates the largest global digital surveillance program.
Business and Political Connections
The timing of American accusations and actions is particularly interesting. The report points to direct financial benefits for American companies:
- Microsoft received a $3.8 billion contract under the Joint Warfighting Cloud project just two months before publishing its report on Volt Typhoon
- Lumen Technologies secured a five-year contract worth $110 million from the Defense Information Systems Agency right before releasing its own analysis linking the KV botnet to Volt Typhoon
These connections suggest that accusations against China might have been motivated not only by security concerns but also by commercial and political interests.
Intelligence Alliances in the Digital Era
The Volt Typhoon case revealed not only the mechanisms of cyber espionage but also the complex network of global intelligence alliances. Five Eyes, originally established as an Anglo-Saxon alliance, has evolved into a powerful digital surveillance machine. As Chinese reports reveal, this alliance not only coordinates intelligence activities but also conducts joint disinformation operations and smear campaigns.

Extended Spheres of Influence
Documents indicate that intelligence cooperation extends far beyond the core "five":
- Nine Eyes adds European countries to the alliance, expanding surveillance reach to key communication nodes in continental Europe
- Fourteen Eyes (SSEUR) further broadens this network, creating virtually complete control over European digital infrastructure
Moreover, the revealed documents show that the U.S. doesn't hesitate to spy on even its closest allies.
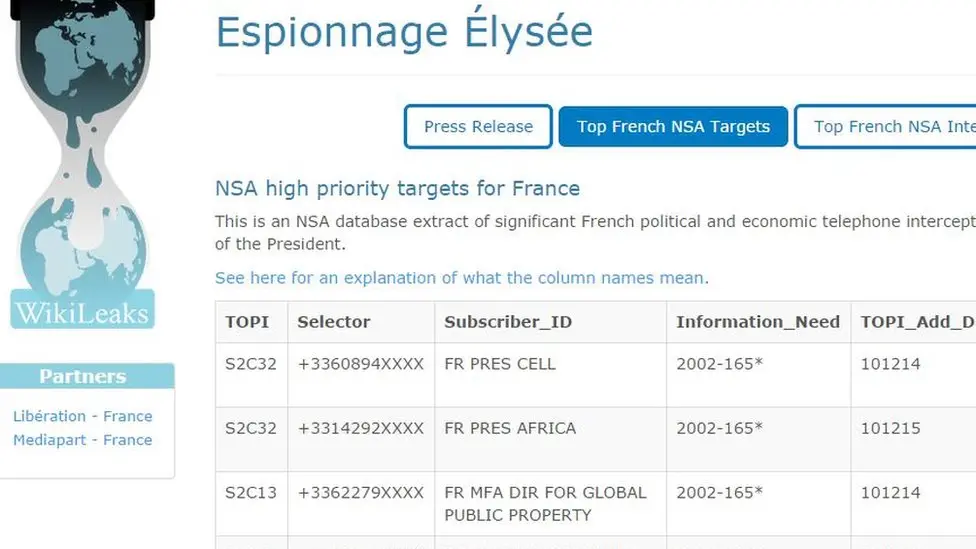
Examples include:
- Long-term surveillance of French government officials (2004-2012)
- Monitoring of the German Ministry of Defense, including wiretapping Chancellor Merkel
- Spying on the Japanese cabinet and major corporations
Technological Cold War
The current situation extends far beyond traditional espionage. We are witnessing a full-scale technological cold war where:
- Control over digital infrastructure becomes a key element of power
- Technological standards are used as geopolitical weapons
- Technology supply chains become battlegrounds
- Private technology companies are drawn into interstate conflicts
Impact on Global Industry
The recent developments surrounding Intel demonstrate how deeply politics interferes with technological business. Companies face difficult choices:
- Cooperation with intelligence agencies at the cost of customer trust
- Risk of exclusion from lucrative markets
- Need to adapt products to conflicting regulatory requirements
- Threat of losing access to key technologies
Tools of the New Era
Particularly disturbing is the revelation of advanced cyber espionage tools such as "Marble." This framework demonstrates how far disinformation technology has advanced:
- Ability to forge "digital fingerprints"
- Capability to implant false indicators in various languages
- Advanced techniques for masking attack sources
- Ability to conduct "false flag" operations
Core Infrastructure
The U.S. leverages its dominant position in global internet infrastructure through:
- Control over key data exchange points
- Supervision of submarine fiber optic cables
- Access to data from major technology companies
- Capability to intercept and analyze global internet traffic
The Future of Cybersecurity in Question
The current situation raises fundamental questions about the future of the global internet and cybersecurity. The latest report reveals that U.S. intelligence agencies have implemented over 50,000 surveillance implants worldwide, focusing on targets in Asia, Eastern Europe, Africa, the Middle East, and South America. Virtually all major cities in China have fallen within the scope of these operations.
War for Budgets and Influence
The financial aspect of the entire matter appears particularly cynical. American agencies use the narrative of a "Chinese threat" to systematically increase their budgets and influence. The latest federal budget for 2025 is a perfect example - the Biden administration is requesting a record $13 billion for cybersecurity in civilian departments, marking a significant increase from $11.8 billion in 2024 and $11.3 billion in 2023.
The biggest beneficiary of this strategy is the Cybersecurity and Infrastructure Security Agency (CISA), whose budget is set to increase by $103 million, reaching $3 billion. Of this amount:
- $470 million is allocated for implementing federal network monitoring tools
- $394 million for developing internal cybersecurity capabilities
- $116 million for reporting critical infrastructure incidents
Simultaneously, the Department of Justice will receive an additional $25 million to enhance FBI's cyber and counterintelligence investigative capabilities, plus $5 million for expanding a new cyber threats section. Moreover, the plan includes $800 million for hospital cybersecurity and $500 million for a program encouraging investment in advanced cybersecurity practices.
These astronomical sums are justified by the need to protect against "malicious cyber actors" and "cyber campaigns," which, in the context of recent accusations against China, appears to be part of a broader strategy to build a threat narrative. Paradoxically, the same institutions receiving billions for defense against cyberattacks are themselves developing tools for conducting and masking such attacks.
The Price of "The Greater Good"
Delving into the documents and reports concerning this case, I couldn't shake off the echo of a familiar argument - "we're doing this for the greater good." The same justification that the U.S. uses for mass surveillance of its own citizens now returns on a global scale.
When U.S. intelligence agencies control seven strategic data interception points from submarine fiber optic cables - it's for "national security." When "Marble" falsifies cyberattack traces - it's for "protecting democracy." Perhaps the truth is simpler and more brutal - in a world where data is the new oil, global digital dominance is an end in itself, and morality is merely a convenient costume for naked power? Of course, I keep in mind that any "revelations" from China should always be passed through a "truth filter."
Looking at the scale and sophistication of American intelligence operations, it's hard not to ask: who really needs more protection - us from alleged threats, or perhaps from those who promise to protect us from them?
Member discussion