Identity-Based Attacks Dominate the Threat Landscape

The latest Cisco Talos Incident Response (Talos IR) report brings disturbing news. In the third quarter of 2024, the incident response team observed a dramatic increase in the effectiveness of attacks targeting digital identity. Moreover, the average ransom amount increased fivefold compared to 2023, reaching a staggering $2 million.
Anatomy of a Modern Breach: 20 Minutes to Disaster
Picture a typical morning at the office. An employee receives an email that looks like any other... but it isn't. In one of the investigated incidents, it took just 20 minutes from clicking a seemingly harmless link to the first unauthorized login. During this time:
- The employee was redirected to a perfect copy of the Microsoft 365 login page
- Unwittingly provided their credentials
- Approved an MFA prompt, thinking it was a routine procedure
- The attacker gained full account access
Nothing extraordinary, just another attack, practically identical to hundreds of others. One might ask, "Why did it take so long?"
Oh Dear... MFA Is No Longer a Security Guarantee
The data from the Talos IR report is clear:
- MFA was bypassed or not fully enabled in 100% of phishing-related incidents
- Over 20% of ransomware victims had no MFA enabled on VPN connections
- Almost 40% of all incidents involved MFA-related issues
"Set-and-forget is a recipe for disaster," warns Craig Williams from Talos IR. "Just installing MFA isn't enough - it must be properly configured and monitored."
The New Era of Ransomware: Evolution of the Threat
Q3 2024 brought a real outbreak of new, highly advanced ransomware variants. Each introduces its own innovations to an already complex threat landscape.

BlackByte: The Spreading Master
BlackByte, one of the most dangerous ransomware variants observed this quarter, introduced breakthrough attack tactics. Unlike traditional ransomware that spreads from a central point, BlackByte operates like a digital pandemic:
- Every infected system becomes a spreading node
- Uses the "bring your own vulnerable driver" (BYOVD) technique to bypass security
- Latest version contains four different vulnerable but legitimately signed drivers
- Successfully exploits the ESXi hypervisor vulnerability (CVE-2024-37085) to take control of entire data centers
- Creates administrative accounts in the "ESX Admin" group during the attack
"Traditional defense methods often prove ineffective against such advanced spreading tactics," explains a Talos IR researcher. Well, yes, just keep your software updated. Only and as much as that.
RCRU64: The Precise Hunter
RCRU64's approach is more methodical:
- Exploits accidentally exposed RDP ports as entry points
- Uses a combination of publicly available tools (fgdump, pwdump) to steal Windows password hashes
- Deploys custom, specialized tools:
- saxcvz.exe for process killing
- close.exe for SQL server shutdown
- First observed use of IObit Unlocker in ransomware attacks
- Meticulously cleans its tracks by clearing system logs
- Selectively encrypts files, avoiding critical system components
DragonForce: Hybrid of Old Powers
DragonForce represents a disturbing trend of "remixing" known malware. The group:
- Uses modified versions of LockBit and Conti ransomware
- Focuses on manufacturing, real estate, and transportation sectors
- Offers a Ransomware-as-a-Service model with 80% affiliate share (keeping 20% commission!)
- Allows affiliated groups to customize tools for specific targets
- Operates primarily in the USA, UK, and Australia
- Has hit 82 different organizations in the past year
RansomHub: Master of Double Extortion
RansomHub, which emerged in February 2024, quickly became one of the most concerning threats:
- Employs two attack models:
- Classic ransomware with data encryption
- Pure data theft without encryption
- Exploits a range of critical vulnerabilities in popular systems:
| Affected Product | Vulnerability | CVSS Score |
|---|---|---|
| Citrix NetScaler ADC and NetScaler Gateway | CVE-2023-3519 | 9.8 (Critical) |
| Fortinet FortiOS and FortiProxy SSL-VPN | CVE-2023-27997 | 9.8 (Critical) |
| Java OpenWire | CVE-2023-46604 | 9.8 (Critical) |
| Atlassian Confluence Data Center and Server | CVE-2023-22515 | 9.8 (Critical) |
| F5 BIG-IP | CVE-2023-46747 | 9.8 (Critical) |
| Fortinet FortiClientEMS | CVE-2023-48788 | 9.8 (Critical) |
| Microsoft Netlogon | CVE-2020-1472 | 10.0 (Critical) |
| Microsoft Windows BITS | CVE-2020-0787 | 7.8 (High) |
| Microsoft SMBv1 | CVE-2017-0144 | 8.8 (High) |
(Yes, you're seeing this right - once again, "just keep updating")
- Primarily targets critical infrastructure:
- Healthcare
- Water management
- Financial services
- Emergency services
- Uses tools like PuTTY, WinSCP, and rclone for data exfiltration
- According to the FBI, attacked over 200 organizations in just 6 months
"We're observing a concerning professionalization of the ransomware world," warns a Talos IR expert. "Groups not only share tools and tactics but also learn from predecessors' successes and failures. This makes each new variant potentially more dangerous than the last."
Disturbing Trend: When Security Tools Become a Threat
This quarter revealed a new, disturbing trend. Attackers aren't just bypassing Endpoint Detection and Response (EDR) systems - specialized tools for threat detection and response - they're actively modifying them:
- Searching networks for security system documentation
- Using legitimate administrative tools to modify EDR
- In some cases, adding their own systems to the victim's security infrastructure
- Modifying monitoring device configurations
For example, EDRKillShifter is responsible for modifications as part of RansomHub operations.
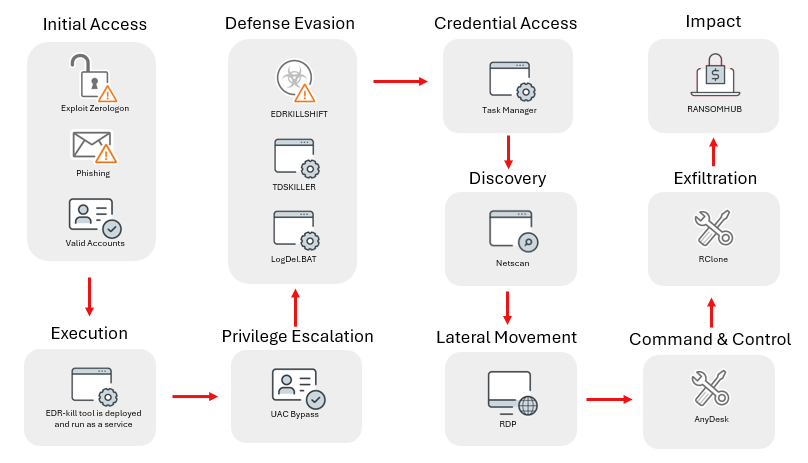
Once again - Set-and-forget doesn't work.
Back to the Future: Why Old Methods Work Again
Password spraying - a technique of trying popular passwords across multiple accounts - is making a comeback. Why? Talos IR experts point to several reasons:
- Growing number of misconfigured MFA systems
- Increased value of stolen credentials on the black market
- Neglected but still active corporate accounts (offboarding procedures aren't working)
- Evolution of attack automation tools
Critical Security Recommendations
In light of these threats, Talos IR experts recommend:

Authentication Modernization
- Implement phishing-resistant MFA (FIDO2 compliant)
- Abandon SMS-based MFA
- Regular MFA configuration audits
- Monitor bypass attempts
Security Infrastructure Protection
- Implement EDR system change monitoring
- Secure technical documentation
- Network segmentation and limited access to administrative tools
- Regular security system integrity verification
Proactive Identity Management

- Automatic detection of inactive accounts
- Implement principle of least privilege
- User Behavior Analytics monitoring
- Quick response to suspicious activities (a ticket to backlog - that's a bit too slow)
Ransomware Protection
- Regular offline backups
- Secure volume shadow copies
- Production network segmentation
- Ransomware incident response plan
Summary: The Arms Race Continues
If you've made it this far - congratulations. You've gone through a quarter summary. Did we discover anything revolutionary? Honestly - no. Should this worry us, or perhaps comfort us?
The Talos IR Q3 2024 report doesn't present breakthrough discoveries - it rather shows how effectively criminals exploit known weaknesses in our security systems. Poorly configured MFA, neglected accounts, vulnerable systems - these are still the same problems that, combined with new attack techniques, become increasingly dangerous.
"It's no longer a question of if we'll be attacked, but when and whether we'll be prepared," aptly summarizes Craig Williams from Talos IR.
The next quarter will undoubtedly bring new challenges. Whether they'll be new ransomware variants or completely new attack methods - we don't know. However, we do know how to prepare. This report isn't just a summary of the last three months - it's primarily a roadmap showing where to strengthen our defenses before it's too late.
For more details, check out the full Cisco Talos IR report at blog.talosintelligence.com.
Member discussion